Deception
Detect threats early in the attack cycle by luring malicious actors away from key assets using decoys, lures, and other deception bait.OVERVIEW
What is Deception?
As attack vectors become increasingly complex, suspicious activity needs to be detected earlier in the attack chain and addressed accordingly. Deception technology helps to attract the malicious actors away from critical assets by distributing a collection of traps and decoys across an organization's infrastructure.
WHY DECEPTION
Role of deception & denial in the attack lifecycle
Security investments are typically made in preventing an attack and exfiltration. However, once attackers bypass the perimeter, they can then move laterally and steal credentials as they establish a foothold, gain privileges, and recon the network in search of their targets. Deception addresses this by placing attractive endpoint lures, data deceptions, and traps throughout the network. Security teams will then gain the visibility required to defend against these attacks and remediate compromised devices.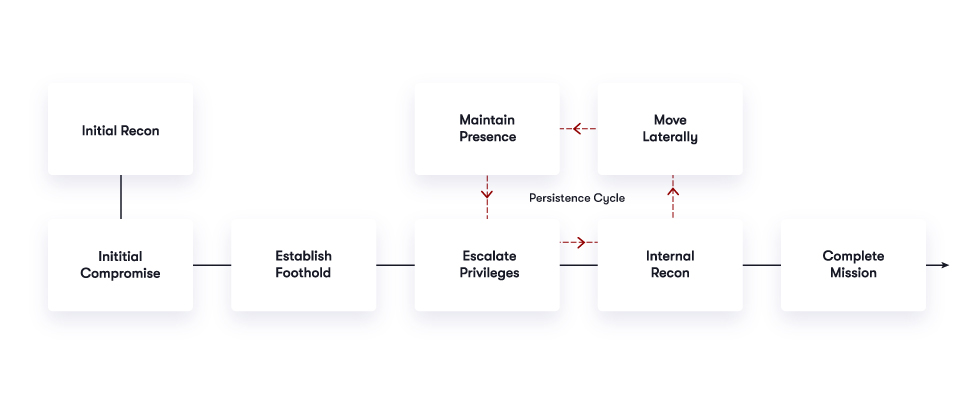
BENEFITS
Reliably detect intruders earlier in the attack chain
As attack vectors become increasingly complex, businesses need to be able to detect suspicious activity earlier in the attack chain and respond accordingly.
1Early Threat Detection
Detection upon engagement with decoy. Not reliant on signatures for threat detection. No pattern matching or database lookup.
2Lateral Movement Threat Detection
Detect early reconnaissance, lateral movement, and activities used by malicious actors to maintain presence within networks.
3Evolving Attack Surface
Decoys to address all attack surfaces including user network, data center, cloud (AWS, Azure, Google, OpenStack), and specialized surfaces like IOT, ICS, POS, SWIFT, Router.
4Man-in-the-Middle Attacks
Early detection of MitM attacks with attack replay to better understand behavior and movement.
5Data & DecoyDoc Deceptions
Data deceptions to misdirect attack. DecoyDocs for counterintelligence on attacker intent with geolocation tracking of opened documents.
6Compliance Breach Investigation, M&A Visibility
Demonstrate in-network detection with forensics to demonstrate resolution.
7Ease of Use
High-fidelity alerts are actionable. Basic and advanced user interfaces are easy to deploy and operate. Automations for attack analysis and incident response.
8Ransomware
Hide and deny ransomware access to local, network, and cloud files and shares. Delay encryption with high-interaction engagement technology to stall the attack.






