
13 May 2025
6 Key Strategies to Implement Zero Trust Architecture

Zero trust architecture (ZTA) is vital for organizations as it fundamentally shifts the security paradigm. Based on the principle "never trust, always verify", the ZTA model ensures that every access request is authenticated and authorized, significantly reducing the risk of data breaches. This proactive stance safeguards sensitive information and fosters a culture of security awareness among employees.
Here we look at zero trust architecture principles, benefits, challenges, and strategies for successful implementation.
Zero Trust Architecture Principles
Unlike traditional methods that trust everything within the network perimeter, zero trust requires constant vigilance and verification.
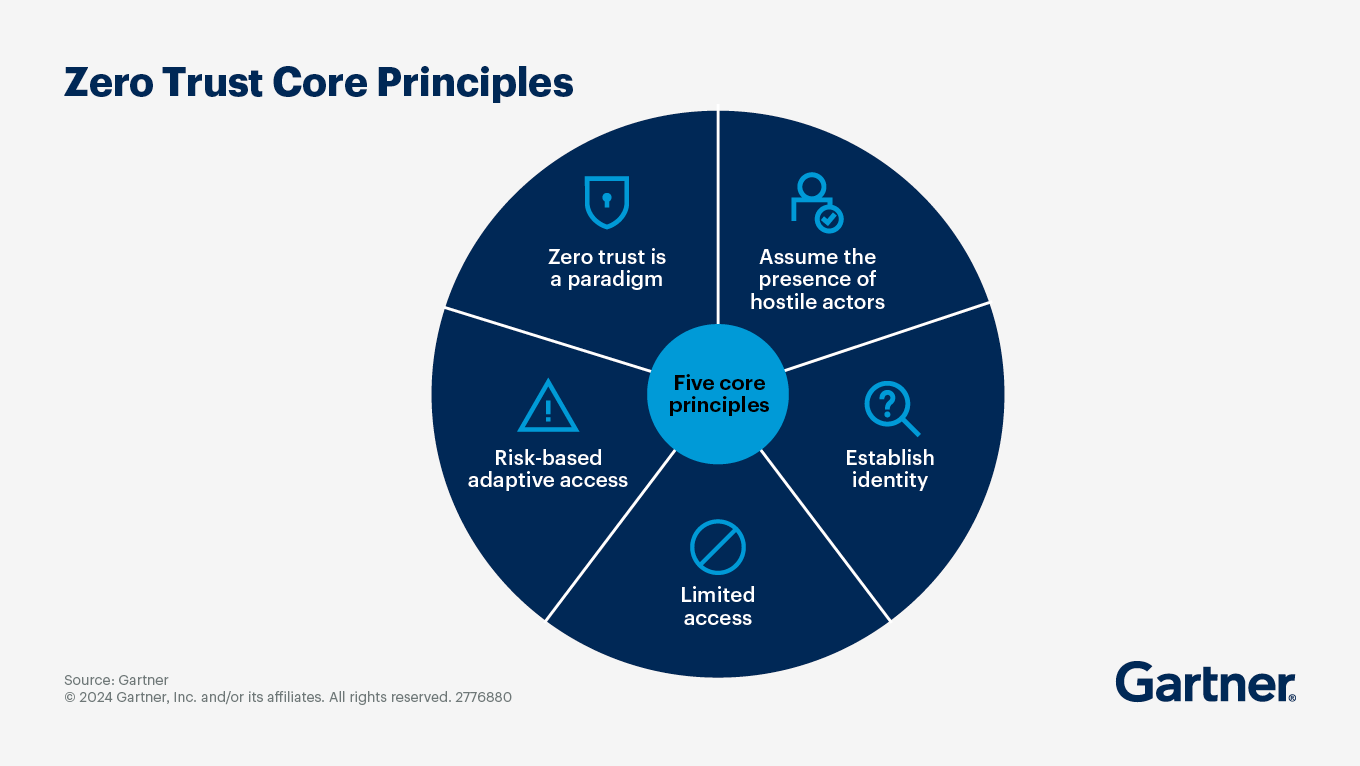
Never Trust, Always Verify
The cornerstone of ZTA is the "never trust, always verify" principle. This approach assumes that threats exist both inside and outside traditional network boundaries. Instead of implicit trust, zero trust requires thorough evaluation of every access request before granting permissions. Each user, device, and network flow must be authenticated and authorized, even if previously verified. This continuous scrutiny creates security control mechanisms that prevent lateral movement of attackers within your environment.
Zero Trust vs Traditional Perimeter Security
The traditional perimeter security approach suffers from significant limitations:
- Trust assumptions: Traditional models automatically trust entities inside the perimeter, creating vulnerability to insider threats and lateral movement once breached.
- Static vs. dynamic: Perimeter security remains static while zero trust continuously evaluates access with adaptive controls.
- Segmentation approach: Rather than securing just the perimeter, zero trust implements microsegmentation down to the workload level, limiting an attacker's ability to move laterally.
- Protection focus: Zero trust protects resources (data, services, applications) rather than network segments, acknowledging that network location is no longer the primary security component.
The traditional model struggles with today's realities - remote work, cloud migration, and BYOD policies have dissolved the clear network boundaries that perimeter security relied upon.
Role of Identity and Access Management (IAM)
Identity and Access Management (IAM) is crucial for effective zero trust implementation. IAM allows organizations to verify user identities, assign privileges, and enforce security policies across resources. It acts as the single source of truth for user and device checks in a ZTA model.
IAM enforces the principle of least privilege access, granting users only necessary permissions, thus minimizing damage from compromised accounts. It also integrates with multifactor and adaptive authentication to verify identity based on behavior and context. This shift from network protection to identity verification helps address security gaps in traditional models.
Benefits of Zero Trust Architecture
Implementing zero trust architecture delivers tangible benefits that go beyond theoretical security improvements.
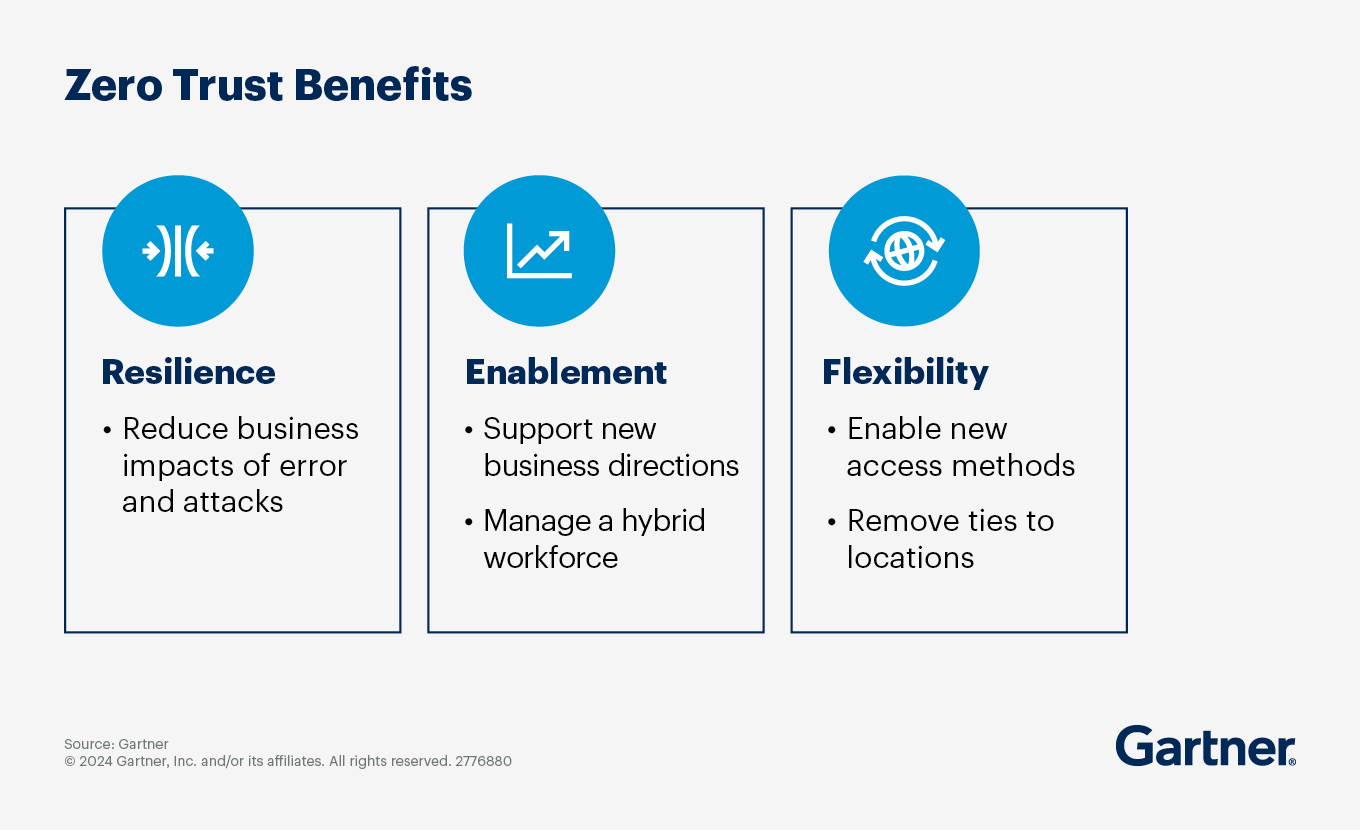
Reduced Attack Surface and Lateral Movement
The ZTA model significantly minimizes the attack surface by enforcing least privilege access principles. Through this approach, users receive only the minimum permissions necessary to perform their tasks, nothing more. This precise control drastically reduces potential entry points for attackers.
Micro-segmentation, a core component of zero trust architecture, logically isolates workloads, applications, and resources within the environment. When attackers breach a network implementing zero trust principles, their ability to move laterally is severely restricted. Instead of gaining unfettered access to network resources, intruders remain confined to a tightly controlled segment.
Improved Visibility and Access Control
A zero trust model substantially enhances visibility into network traffic and user activities. Through continuous monitoring and logging, organizations gain unprecedented transparency over their environments. This improved visibility allows organizations to detect anomalies faster and respond to threats more effectively.
Regulatory Compliance and Data Protection
The adoption of zero trust principles aligns directly with various regulatory requirements focused on data protection and privacy. Indeed, organizations implementing zero trust architecture often find they already meet certain compliance conditions or can easily build upon their existing framework to achieve compliance.
In essence, zero trust security doesn't just improve your security posture, it also functions as an insurance policy against lost or stolen data.
Challenges for Zero Trust Architecture Implementation
Transitioning to a zero trust architecture demands significant change across technical infrastructure, resources, and policy frameworks.
Legacy System Integration
Older systems create fundamental compatibility challenges since they weren't designed with zero trust principles in mind. Legacy infrastructure often lacks the necessary flexibility to support modern security measures, primarily because they were built for implicit trust models. These systems frequently struggle with hardcoded credentials, outdated protocols, limited logging capabilities, and monolithic architectures.
High Initial Cost and Resource Allocation
The financial investment for zero trust implementation is a major barrier. Organizations spend an average of MYR 3 million when adopting a zero trust architecture. Additionally, half of cybersecurity professionals estimate implementation takes 7-11 months.
Resource constraints extend beyond money alone. The implementation journey requires skilled architects to design appropriate systems, additional infrastructure, and training and education costs for staff.
Complexity in Policy Management Across Environments
Perhaps the most persistent challenge is managing zero trust policies across diverse environments. In multi-cloud settings, policy management often becomes the main obstacle because each cloud platform has unique tools and security requirements, resulting in numerous consistency issues.
6 Strategies to Implement Zero Trust Architecture
Implementing a Zero Trust architecture involves a systematic approach. Here are some key strategies:
1. Define the Protect Surface
Unlike the traditional attack surface, which can be vast and hard to secure, the protect surface is smaller and more manageable. Organizations need to identify and categorize their most crucial assets, including sensitive data, critical applications, and essential services. By pinpointing these components, organizations can focus their security efforts where they matter most.
It's also important to understand how data flows between these assets. Organizations should map the interactions between users, devices, and applications to identify potential vulnerabilities. This mapping process helps establish clear access controls and monitoring requirements.
2. Establish a Zero Trust Policy
A well-defined Zero Trust policy outlines the rules governing access to network resources. The policy should specify the requirements for identity verification, access approval criteria, and procedures for continuous monitoring and response to security incidents.
ZTA policies typically encompass protocols for multi-factor authentication, standards for encryption, access control lists, and network segmentation strategies. These policies also specify the duties and accountabilities of various stakeholders, including end users, system administrators, and cybersecurity personnel, in ensuring ongoing network security maintenance.
3. Strengthening Endpoint Security
Endpoints, like laptops, smartphones, and IoT devices, are often the weakest links in network security. Organizations need to use robust endpoint security measures, including:
- Endpoint Detection and Response (EDR): These solutions monitor and respond to threats in real time.
- Regular Updates and Patching: Keeping all devices updated with the latest security fixes is important to reduce weaknesses.
- Implementing Device Compliance Checks: Before letting devices connect to the network, organizations should check if they are compliant with security policies.
4. Enhancing Monitoring and Analytics
Advanced monitoring tools that provide real-time visibility into network traffic and user behavior must be utilized. These tools should be capable of detecting anomalies and potential threats as they occur.
Analytics are also crucial for identifying patterns and trends that may indicate malicious activity. By incorporating machine learning and artificial intelligence, organizations can improve their ability to identify patterns indicative of malicious activity. These technologies can analyze vast amounts of data to detect unusual behavior and alert security teams promptly.
5. Automating Security Responses
Automation can significantly reduce the time it takes to identify and mitigate threats. Security Orchestration, Automation, and Response (SOAR) platforms can streamline security operations by automating repetitive tasks and coordinating response efforts.
Automated security responses enable organizations to quickly isolate compromised systems and execute predefined response actions. This rapid response capability is crucial for minimizing the impact of security incidents.
6. Leveraging Industry Frameworks and Standards
Organizations can benefit from established frameworks such as the National Institute of Standards and Technology (NIST) Zero Trust Architecture. These guidelines provide best practices for designing and implementing a ZTA model, ensuring compliance with regulatory requirements.
Conclusion
Ultimately, zero trust security represents more than just a technological shift—it embodies a fundamental change in security philosophy. Organizations must embrace this security paradigm not as a single product implementation but as an ongoing journey of continuous verification, least privilege enforcement, and adaptive security controls.
Looking to improve your cybersecurity posture? Contact us to see how we can help.


