
11 April 2025
Zero Trust Architecture: Why it Matters in 2025

With over 26 million web threats recorded in South East Asia during the first half of 2024, organizations are turning to zero trust architecture as their primary defense against evolving cyber threats. Introduced in 2010 by John Kindervag, a former analyst at Forrester Research, this security framework operates on a simple yet powerful principle: "never trust, always verify."
Many organizations worldwide have already implemented zero trust architecture, including tech giants like Microsoft, Google, and Amazon. This widespread adoption stems from the framework's effectiveness in preventing lateral movement during breaches and its crucial role in securing remote access - particularly important as businesses adapt to hybrid work models. Furthermore, the framework helps organizations comply with regulations like HIPAA, GDPR, and CCPA while protecting their expanding cloud environments.
In this article, we'll explore what zero trust architecture is, why traditional security models fall short, and how this approach delivers strategic advantages beyond security. We'll also examine real-world implementation examples and methods to measure success.
What is Zero Trust Architecture?
Zero trust architecture (ZTA) represents a fundamental shift in cybersecurity design. Unlike traditional approaches that trusted everything inside a network perimeter, ZTA operates on the assumption that threats exist both inside and outside organizational boundaries.
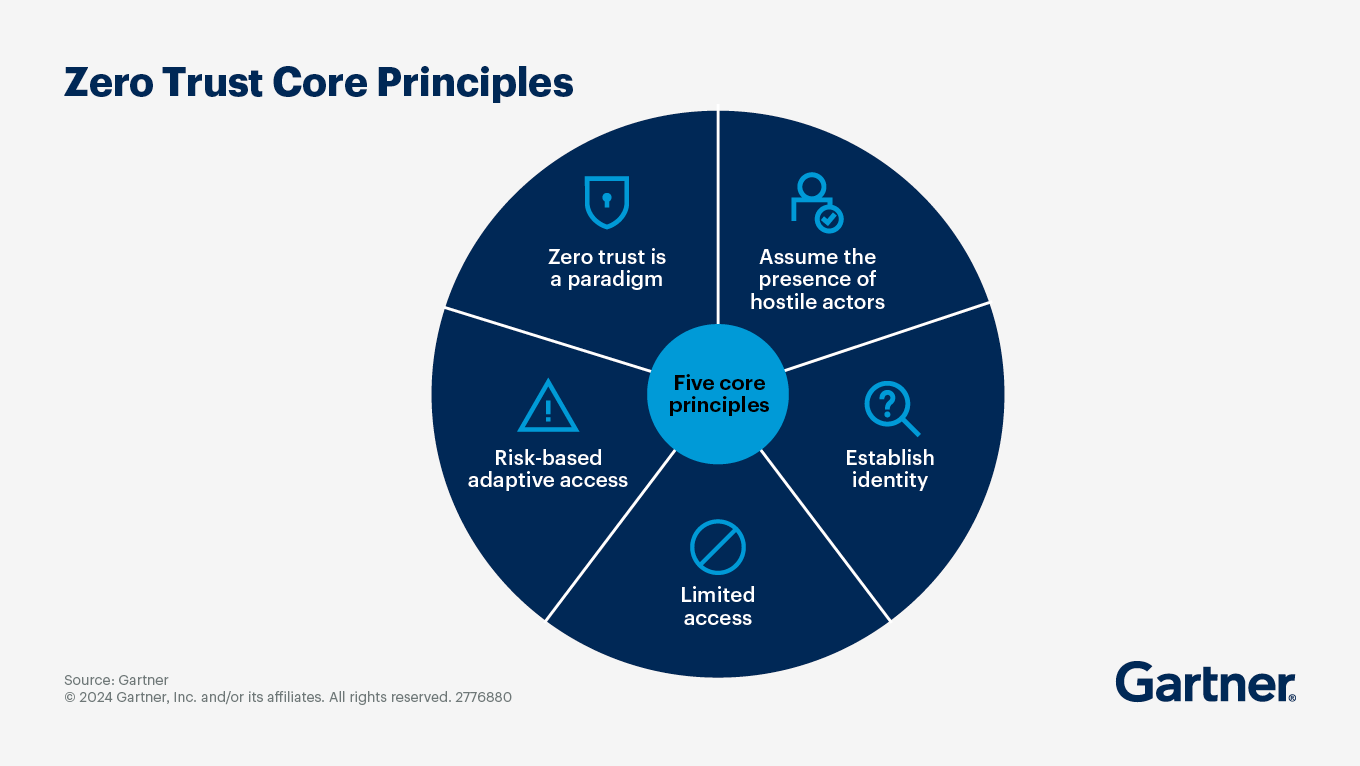
Key Components of a Zero Trust Framework
A comprehensive zero trust architecture incorporates several essential components:
- Strong Identity Verification: Every access request begins with authenticating the identity of the user or entity attempting access
- Micro-segmentation: Breaking down networks into isolated segments to limit lateral movement for attackers
- Least Privilege Access: Users receive only the minimum access necessary to perform their functions
- Continuous Monitoring: Systems actively track all activities to identify anomalies and suspicious behaviours
- Multi-Factor Authentication: Multiple verification methods ensure credentials alone aren't sufficient for access
- Policy-Based Access Controls: Access decisions based on dynamic policies rather than static rules
ZTA outlines how these components are implemented throughout systems, networks, and workflows to ensure that no user, device, or application gains access without thorough validation.
Why Traditional Security Models Are Failing Organizations
Traditional perimeter-based security models have become increasingly ineffective in today's distributed, hybrid, and cloud-first business landscape. Extending network perimeters to accommodate remote work, mobile devices, SaaS applications, and third-party partnerships has resulted in higher costs, greater complexity, reduced productivity, slower digital transformation, and most importantly, elevated cybersecurity risks.
Four significant vulnerabilities plague traditional security models:
- Expanded attack surface: Traditional tools like firewalls and VPNs inherently expose IP addresses to the public internet, creating entry points that cybercriminals can target and exploit.
- Inadequate threat detection: Appliance-based security solutions, whether hardware or virtual, lack the scalability needed to properly inspect encrypted traffic where most modern threats conceal themselves. Consequently, many attacks pass through defences unnoticed.
- Unconstrained lateral movement: Traditional approaches grant network access to provide application access, creating environments of implicit trust with excessive permissions. This allows threats to move freely across connected systems, amplifying the scope of breaches.
- Ineffective data protection: After locating sensitive information, attackers typically attempt exfiltration through encrypted channels, knowing that conventional appliance-based security will fail to secure such traffic.
These limitations render traditional security frameworks not only ineffective against contemporary threats but also poorly aligned with today's dynamic, distributed IT environments. Organizations require a fundamentally different approach, one that eliminates implicit trust and positions security at the core of every connection.
Business Benefits Beyond Security: The Strategic Advantage
Beyond merely protecting digital assets, zero trust architecture delivers substantial business advantages that extend throughout an organization's operations. Forward-thinking companies are discovering how this security paradigm drives growth alongside enhanced protection.
Enabling Digital Transformation Initiatives
Zero trust architecture serves as a catalyst for digital transformation by removing traditional barriers to innovation. Instead of simply migrating applications to the cloud, organizations must transform their network and security infrastructure to realise the full potential of digitisation. Over 90% of IT leaders who have started cloud migration have already implemented or are implementing a zero trust strategy.
A comprehensive zero trust framework enables organizations to safely adopt cloud computing, remote work capabilities, IoT/OT devices, and other modern technologies.
Supporting Remote and Hybrid Work Models
The shift toward hybrid work has forced organizations to rapidly adapt as employees access resources from various locations and devices. Zero trust architecture directly addresses this challenge by securing connections regardless of location, provided employees authenticate properly on compliant devices.
Reducing Operational Costs Through Streamlined Access
Zero trust architecture delivers significant cost benefits through several mechanisms:
- Consolidated security: By replacing disjointed security approaches with a cohesive model, organizations can reduce the overall cost of compliance.
- Limited attack surface: Principles of least privilege and separation of duties create a more focused technology landscape, reducing breach likelihood and costs.
- Simplified infrastructure: Zero trust can cut security appliance hardware costs by up to 90% while shifting capital expenditures to operational expenditures.
Zero Trust Architecture Examples Across Industries
Across key industries, zero trust architecture implementations showcase how this framework adapts to unique security challenges while delivering measurable benefits.
Financial Services: Protecting High-Value Transactions
Financial institutions represent prime targets for cybercriminals due to their valuable digital assets. These organizations operate in data-rich environments that constantly shift, opening new vulnerabilities. By implementing zero trust, banks can protect high-value transactions through continuous authentication and strict access controls.
A key advantage for financial services is zero trust's ability to wrap security initiatives into a single strategy that addresses industry-specific challenges. Specifically, banks must comply with regulations like PCI DSS, which was built with a zero trust mindset and requires stronger authentication standards for payment and control access logins.
Although financial institutions often maintain legacy systems that run high-value transactions, zero trust helps overcome this challenge by focusing on identity protection rather than network location.
Healthcare: Securing Patient Data While Maintaining Access
The healthcare industry faces unique security pressures, with medical records fetching up to RM1,000 per record on the dark web, 47 times more valuable than payment card information. Yet the sector must balance security with accessibility for multiple user types.
Healthcare organizations are turning to zero trust to manage access to sensitive applications like electronic health records which have seen adoption skyrocket. First, these systems verify every user regardless of role. Second, they apply contextual authentication that considers factors like user behaviour patterns.
The stakes are exceptionally high. 36% of healthcare facilities reported increased medical complications due to ransomware attacks. Thus, zero trust microsegmentation offers a practical approach to prevent lateral movement during breaches.
Manufacturing: Securing Supply Chain and OT/IT Convergence
Manufacturing has become the most targeted industry for three consecutive years, with over 25% of security incidents involving manufacturers. The convergence of IT and operational technology (OT) networks presents unique challenges as antiquated equipment and legacy operating systems become backdoors into enterprise systems.
Zero Trust Network Access offers manufacturers powerful protection by:
- Reducing attack surfaces through least privilege access
- Providing granular control over factory floor assets
- Establishing secure, encrypted tunnels between users and resources
This approach effectively shields industrial systems from rising cyberthreats while supporting digital transformation. Despite implementation challenges, manufacturers find immediate benefits in improved security posture and greater protection of intellectual property.
Conclusion
As cyber threats continue evolving, zero trust architecture provides organizations the foundation needed for robust security and business growth. The framework's proven track record across industries, measurable benefits, and adaptability to emerging challenges position it as an essential approach for modern enterprise security.
Looking to improve your cybersecurity posture? Contact us to see how we can help.


